Takedowns
How ThreatWatch360 Handles Takedowns?
Key Feature
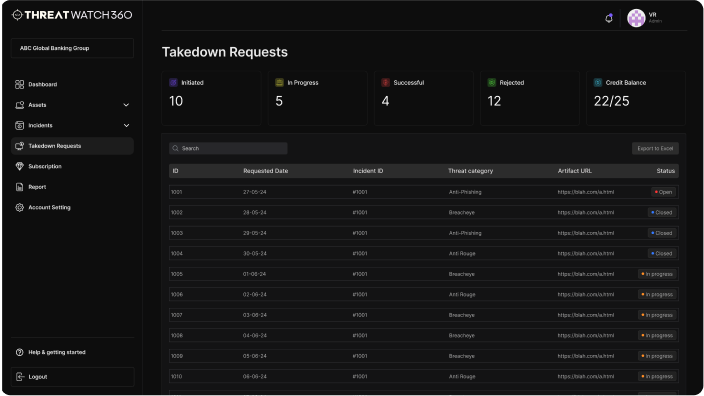
Takedown Requests Submitted to ThreatWatch360
ThreatWatch360 identifies and prioritizes diverse threats for swift action, including:
- Malicious domains and phishing URLs
- Fraudulent mobile apps and marketplace listings
- Copyright-infringing, harmful, or abusive content
Immediate Action
Automated Tagging and Takedown Requests: Threats are categorized and sent to the relevant platforms, hosting providers, or registrars for disruption and removal.
Proactive Mitigation Measures: Blocking malicious domains and preventing further spread of harmful content.
Threat Intelligence Distribution: Sharing actionable threat intelligence with security blacklists, ISPs, and other stakeholders to bolster defenses.
Threats Resolved at Scale
Neutralizing Attacker Infrastructure: Domains, phishing emails, apps, and content are dismantled to disrupt ongoing threats.
Full Process Transparency: A centralized dashboard provides complete visibility and control over takedown requests.
Detailed Reporting: Status updates, tracking logs, and resolution reports offer clear insights into the takedown process.
Why Choose ThreatWatch360?
- Speed & Efficiency:: Immediate identification, action, and resolution.
- Scalable Operations: Handle thousands of takedowns simultaneously across global platforms
- Comprehensive Protection: End-to-end monitoring, disruption, and reporting
Protect your brand, assets, and customers from digital threats with ThreatWatch360’s Takedown as a Service

Get Started With Takedowns
Take Action Now!
Protect your brand, assets, and customers from evolving digital threats with ThreatWatch360.
- Request a Free Demo to see our takedown process in action.
- Speak to our experts to tailor solutions for your business.
- Safeguard your brand’s reputation with 24/7 threat monitoring and removal.
Frequently Asked Questions